
If you dislike corporate buzzwords (who doesn’t?) then you’ll no doubt shudder when you hear “Zero Trust” when discussing cybersecurity. This article is designed to explain in simple terms exactly what Zero Trust is, why we should care, and what your business needs to know and do about it.
Practically every industry in the world is the same, awash with acronyms and corporate buzzwords that leave many dazed and confused. If you’re like me, you dislike buzzwords and prefer to speak straight to the point. Zero Trust is another concept that is commonplace within the IT world today, and you may have heard of it if you’re job role connects to IT, technology, data protection or regulatory compliance. But what does it mean?
Zero Trust isn’t a product; it’s not something you can buy off the shelf. It’s a methodology, a framework, a way of working. Zero Trust is a cybersecurity strategy that assumes no user, device or application, either inside or outside the network, should be trusted by default. There are three key pillars of Zero Trust:
• Verify Explicitly: Authenticate every user and device using multiple data points.
• Use Least Privilege Access: Grant only the minimum access necessary for each role.
• Assume Breach: Design systems with the expectation that breaches can and will happen.
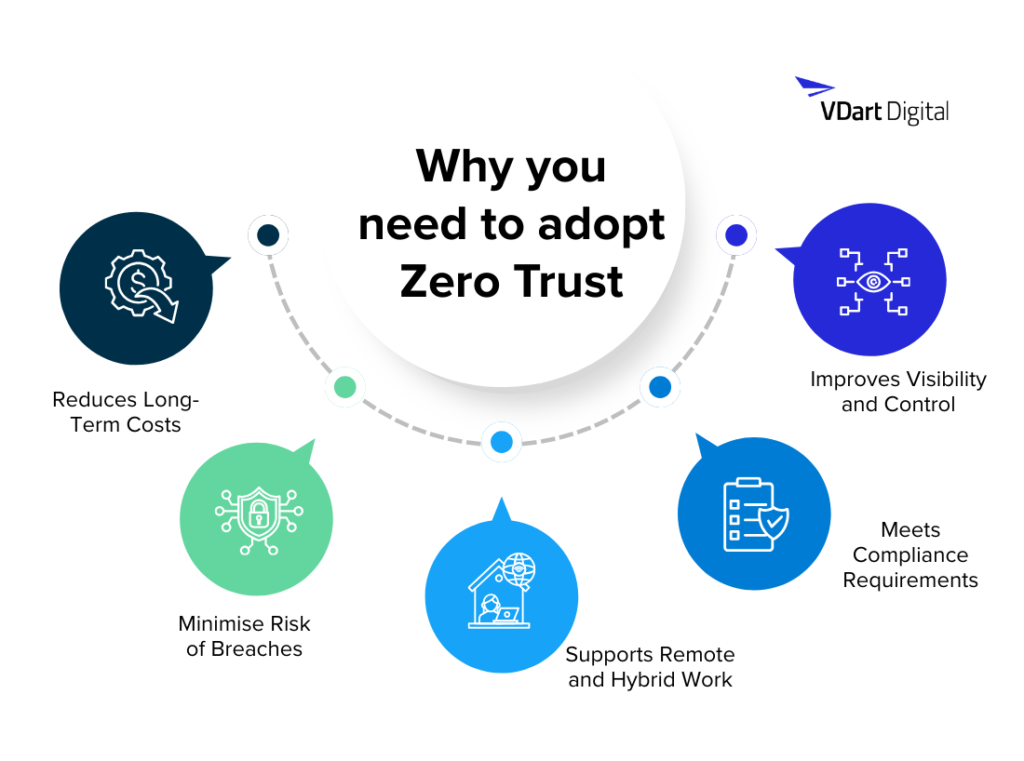
Why Businesses need to adopt Zero Trust
Minimizes Risk of Breaches
Supports Remote and Hybrid Work
Zero Trust enables secure access from anywhere, making it ideal for businesses with remote employees, contractors, or BYOD (Bring Your Own Device) policies.
Improves Visibility and Control
With granular access logs and real-time monitoring, businesses gain deep insights into who is accessing what, when, and how, helping identify vulnerabilities before they’re exploited.
Reduces Long-Term Costs
While implementing Zero Trust requires upfront investment, it significantly lowers the financial impact of breaches, downtime, and regulatory fines.
Meets Compliance Requirements
Regulatory frameworks like GDPR, HIPAA, and CMMC increasingly demand robust identity and access controls. Zero Trust helps businesses stay compliant and audit-ready.
How can I get started with Zero Trust Cybersecurity?
Adopting Zero Trust doesn’t require a complete overhaul overnight. Start with these simple principles:
• Secure the User through strong password policies, MFA and biometrics
• Secure the Device through Conditional Access policies and an EDR (endpoint detection and response) solution
• Secure the Data through Microsoft Purview controls
These steps lay the foundation for a scalable Zero Trust architecture that grows with your business.
In a world where cyber threats evolve daily, businesses that embrace Zero Trust are better equipped to protect their data, empower their teams, and build trust with customers.
Zero Trust Frequently Asked Questions
Zero Trust means not automatically trusting anyone or anything trying to access your systems, even if they’re already inside your network. Every user, device, and app must prove who they are before they’re allowed in. It’s about being careful, not paranoid.
Because the way we work has changed. People log in from home, on personal devices, and across cloud services. Zero Trust helps protect your data wherever your team works and makes it much harder for attackers to move around unnoticed.
No. It’s not about blaming people. It’s about protecting everyone. Even good employees can have their accounts hacked. Zero Trust just means everyone follows the same security checks so one mistake doesn’t put the whole company at risk.
Not at all. Smaller businesses can benefit even more. You don’t need a full-blown enterprise setup, just start with the basics like multi-factor authentication (MFA), device management, and clear access policies. Those small steps make a huge difference.
There’s no “one size fits all.” It depends on your systems and what you already have in place. The best approach is gradually secure your users, devices, and data first, then build from there. Think of it as improving your security one layer at a time.
There are three simple rules:
• Verify explicitly: Always check who’s trying to get in and from where.
• Use least privilege: Give people access only to what they need, no more.
• Assume breach: Plan as if someone’s already inside, so you’re ready when things go wrong.
Zero Trust is made for it. When people work from different places and devices, it’s important to know every login is genuine. With tools like conditional access and MFA, your team can work from anywhere without compromising security.
Yes. It naturally supports frameworks like GDPR and ISO 27001. By verifying access and monitoring activity, you’re already ticking many of the compliance boxes. Plus, it gives you the audit trail you’ll need if regulators come knocking.
Some common ones include:
• Multi-Factor Authentication (MFA) for secure logins
• Endpoint Detection and Response (EDR) for monitoring devices
• Conditional Access to control when and how people log in
• Data protection tools like Microsoft Purview for sensitive info
You don’t have to deploy everything at once — build the setup that fits your business.
At VDart IT Services, we help businesses of all sizes put Zero Trust into practice. We can assess where you are now, plug any security gaps, and guide you step by step. The goal isn’t to sell you a product, it’s to make sure your systems and people stay safe.
Author Name: Bobby Goel








